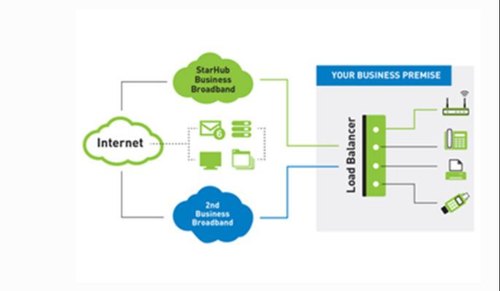
Link Load Balancer / Server Load Balancer / SSL Acceleration
Link load balancing provides advanced failover and bandwidth management for multiple WAN connections to assure continuous operation of enterprise applications and cloud services in the event that one or more ISP links become unavailable or slow to respond. SLB provides numerous benefits that ease overall administration of TCP/UDP applications on servers as well as increase their performance and reliability.
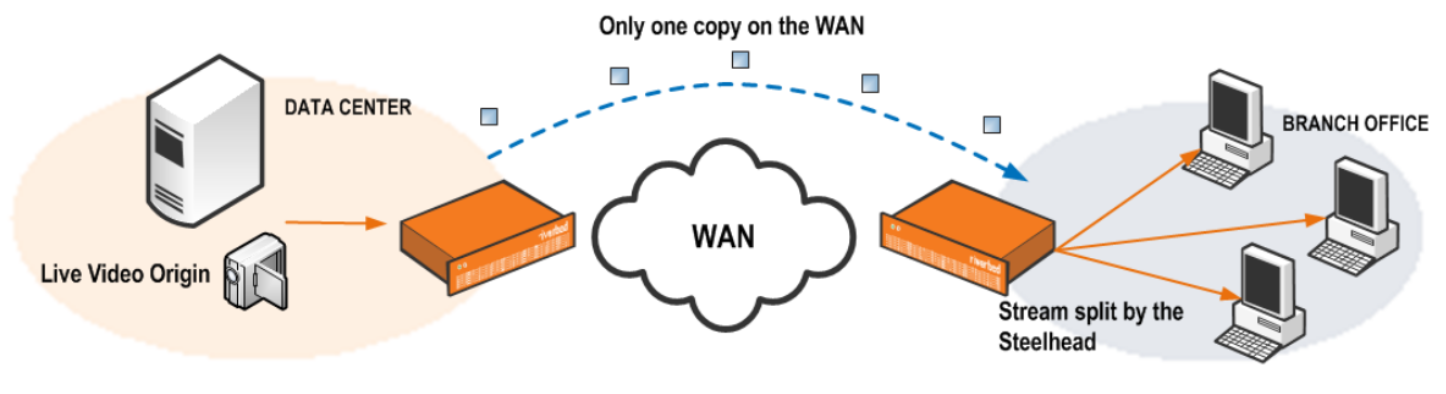
WAN Optimization
WAN optimization reduces bandwidth usage between data centers and client devices by applying advanced compression algorithm, data caching and other techniques to reduce bandwidth usages, better application performance and reduces the high costs of WAN links between data centers.

IPV4 to IPV6
IPv6 is the next generation Internet Protocol (IP) address standard intended to supplement and eventually replace IPv4. IPv4 is running out of numbers & Techium Solution provide IPv4 to Ipv6 migration solutions from the world leader in this space.

Voice & Video Collaboration
Good video and voice traffic for unified communications needs to be protected but recreational video must be controlled. The network must deliver a predictable experience for video and voice while supporting other applications that compete for bandwidth on the same link.

WAN Orchestration
Combine WAN- Analytics, Recommendation and Action all in one platform. Orchestrating these key WAN capabilities in harmony is the only way to solve the network problems in any organization.

Server & Storage ( SAN / NAS / Virtualization/ SSD )
The permanent holding place for digital data, until purposely erased. Storage is a repository that retains its content without power and includes magnetic disks, solid state drives (SSDs) and flash drives. SAN (Storage Area Network) and NAS (Network-attached storage) are both network-based storage solutions. A SAN stores data at the block level, while NAS accesses data as files.
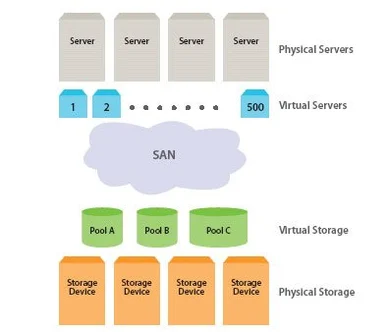
Virtualization of Storage and Server
Companies are increasingly leveraging technology to address the explosion in demand created by virtualization and the shift toward the cloud to cut edge tools to overcome back- and front-office challenges such as meeting server and storage needs, managing storage assets and complex infrastructure, fulfilment, forecasting, supply chain execution, monitoring customer loyalty, and leveraging big data and analytics.

Enterprise Password Management / Privileged Identity Management/ Security Policy Mgmt
Manage and protect your organization’s most vulnerable secrets: your privileged passwords. Password management software offers users secure access to passwords and other privileged information Management (PIM).
Security Policy Management
Automated firewall rule analysis, network device configuration checks, and change management enable continuous compliance with 80 percent reduction in costs Keeping firewalls, routers, switches, and other devices configured to minimize risks and stay compliant with security policies is time consuming and costly for large networks.

Network Performance Management / Network Forensics
Solutions combine intelligent analysis, intuitive workflows, and continuous data collection to empower network and security professionals to visualize, troubleshoot, and analyze the networks that organizations depend on. Network Forensic analysis takes traditional protocol analysis to the next level by extending the duration that the analyzer can capture packets with the latest capture, storage and analysis technology. A Network Forensic Analyzer most commonly called a Network Recorder, captures and stores all traffic so that it can be retrieved for analysis later.

Business Service Management ( BSM)
Business service management (BSM) software, tools and technologies are being used to facilitate success. It’s a general practitioner for the IT infrastructure. By pointing out the problematic tiers, the service management solution ensures that only the right administrators need be involved in fixing a problem.

Application Performance Management
Tools and processes responsible for monitoring and managing the performance and availability of software applications. APM tools alert IT staff to disruptions in availability and/or quality &include traditional non-connected applications, Web-enabled applications, streaming apps and cloud applications.
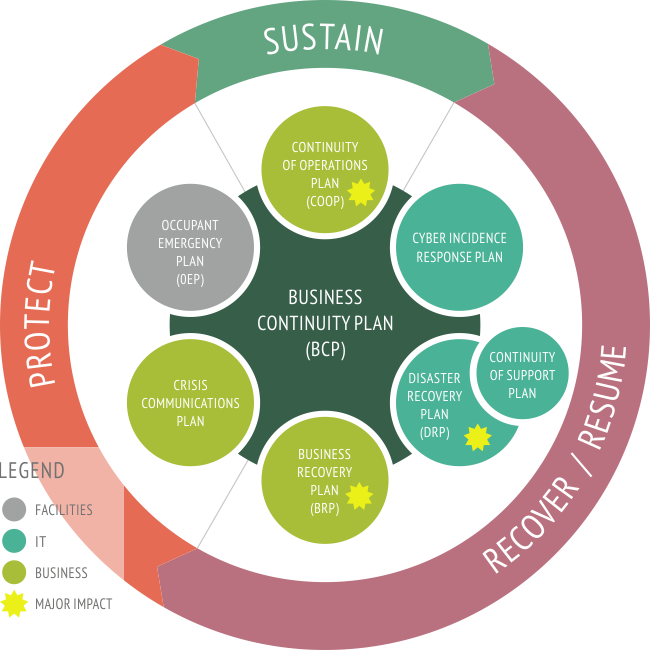
Business continuity and IT recovery
Disaster recovery (DR) is a holistic strategy including people, processes, policies, and technologies. It is the process, policies and procedures that are related to preparing for recovery or continuation of technology infrastructure & it also ensure that information infrastructure that runs the business is disaster proof is extremely critical considering the cost implications of system downtimes.
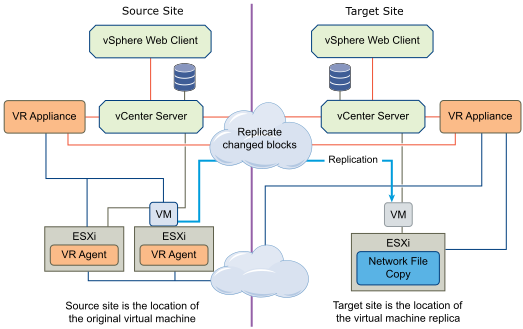
File replication and Data Availability
Solutions includes both Volume Replicator and File Replicator to provide world-class, cost effective continuous data replication enabling rapid recovery of critical applications at remote recovery sites across any distance using IP networks.