SOAR
Security orchestration, automation and response (SOAR) technology helps coordinate, execute and automate tasks between various people and tools, allowing companies to respond quickly to cybersecurity attacks and improve their overall security posture. SOAR tools use security “playbooks” to automate and coordinate workflows that may include any number of disparate security tools as well as human tasks.

SIEM
A SIEM system centralizes the storage and interpretation of logs and allows near real-time analysis which enables security personnel to take defensive actions more quickly. A SIEM system collects data into a central repository for trend analysis and provides automated reporting for compliance and centralized reporting. A SIEM system collects logs and other security-related documentation for analysis.
Virtualization and Cloud Security
Cloud and Virtualization gives you agility and efficiency to instantly roll out new services and expand your infrastructure. But the lack of physical control, or defined entrance and egress points, bring a whole host of cloud security issues – data co-mingling, privileged user abuse, snapshots and backups, data deletion, data leakage, geographic regulatory requirements, cloud super-admins, and many more.

Unified Threat Management
Techium Solution offer a compelling value proposition for smaller organizations and branch offices: A single, low cost, and easy-to-manage appliance that can replace multiple security software products running on separate servers.
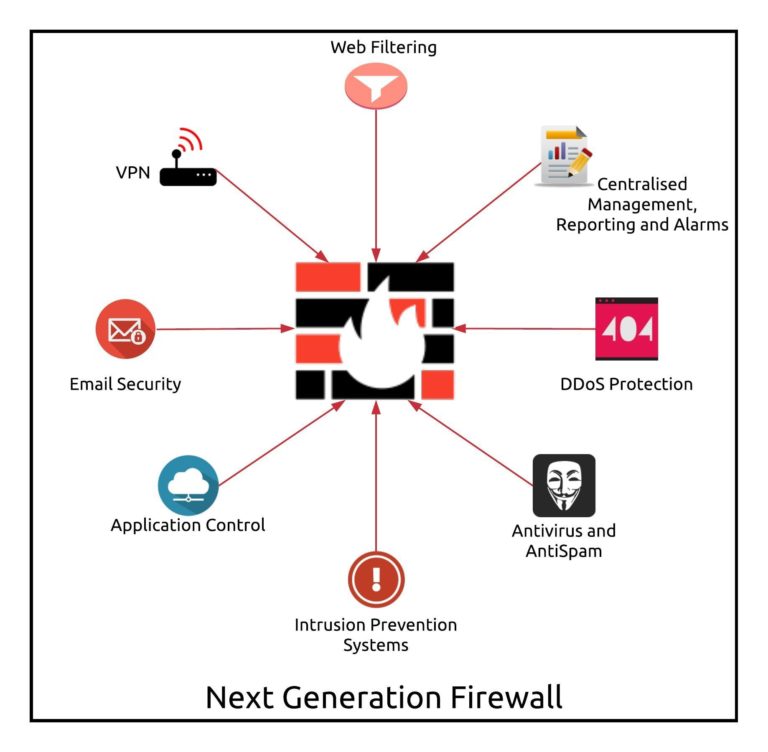
Next Generation Enterprise Firewall
Techium Solution provides customers of all sizes with the latest data and network security protection in a single integrated next generation firewall platform, reducing complexity and lowering the total cost of ownership.

Next Generation Intrusion Prevention
Techium Solution provides customers in-line, real-time Next Generation Intrusion Prevention System (NGIPS) to defend critical data and applications from advanced attacks without affecting performance and productivity.
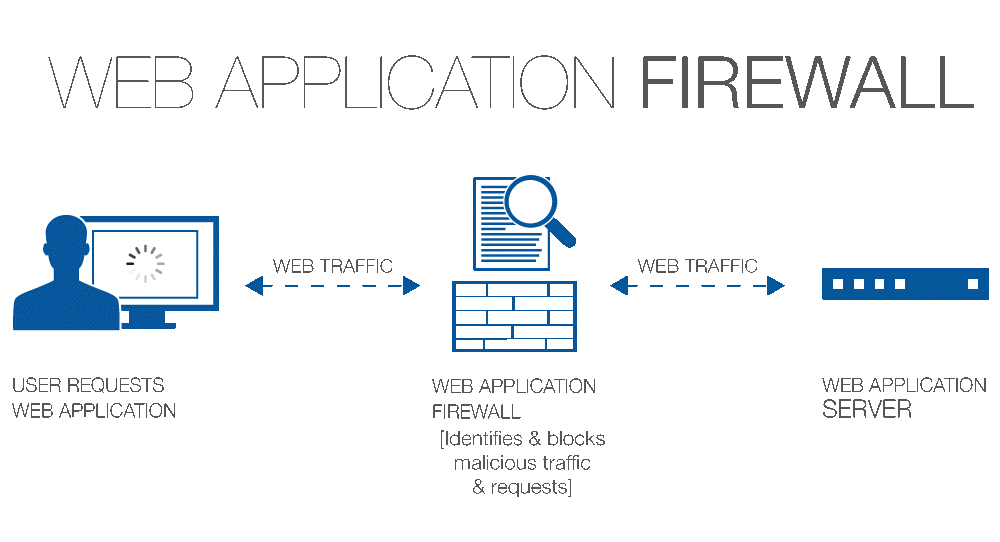
Web Application Firewall
Techium Solution provides WAF Firewall analyzes all user access to your business-critical web applications and protects your applications and their data from attacks. Web Application Firewall acts upon dangers maliciously woven into innocent-looking website traffic; vulnerability attacks such as SQL injection, cross-site scripting etc.

End point/Web/ Mobile/Email security
Techium Solution provides Endpoint/Web/Mobile/Email security to secure endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns. Endpoint security systems protect these endpoints on a network or in the cloud from cybersecurity threats.

Web/Email Content Filtering
Content Filtering evaluates inbound and outbound Web& Email Traffic on the basis of user-defined rules, which contains a list of keywords and phrases. Content filtering evaluates the header and/or content of messages by comparing the messages with the list of keywords and take action to prevent the undesirable content from being delivered.
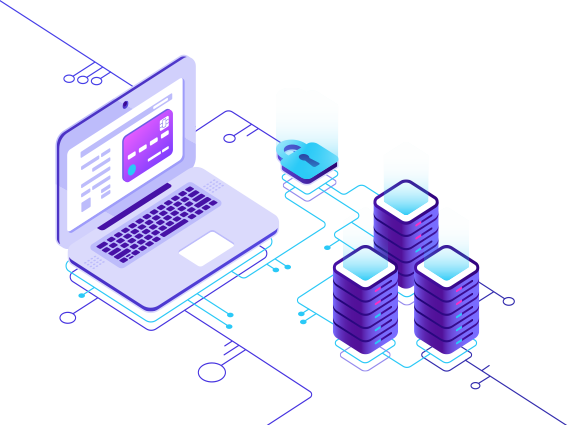
Data Loss Prevention
Data Loss Prevention is a family of solutions designed to minimize the risk of information loss and improve your visibility of data usage patterns and risky business processes— so your private information remains secure. You’ll gain broad coverage, high performance, and deployment flexibility needed to comply with regulatory mandates.
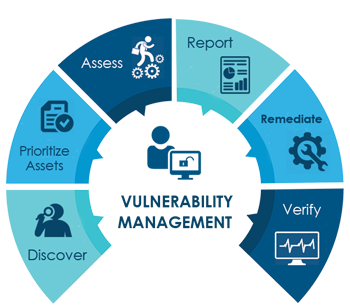
Vulnerability & Compliance Management
Vulnerability and Compliance Management (VCM) solutions help to identify compliance requirements and deliver real-time insight into vulnerabilities and security policies, while reducing the pain of manual remediation.
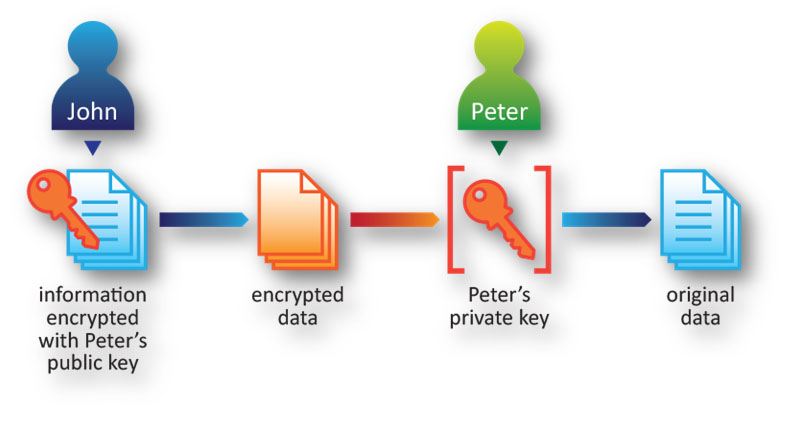
Information Right Management
Your data is all over the place with vendors and partners, on the cloud, and on mobile devices. It is becoming more and more challenging to secure and control all of it all the time. You need something that empowers your ‘borderless enterprise’ to secure sensitive information – on any network, on any platform, and on any device.
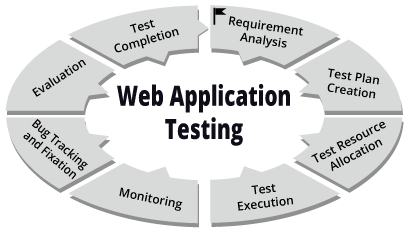
Web Application testing
An automated dynamic testing tool that mimics real-world hacking techniques and attacks, and provides comprehensive dynamic analysis of complex web applications and services.

Static Code Analyzing
You may have software that’s built in-house, outsourced, or delivered from the open source. Code Analysis is effective approach to assure application security for your software requires resolution of potentially exploitable vulnerabilities.
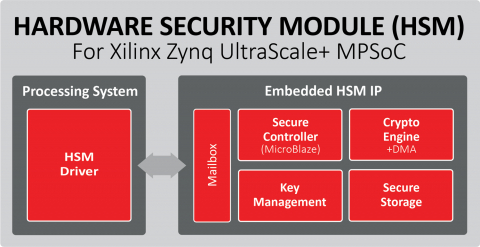
Hardware Security Module ( HSM)
HSM is a physical computing device that safeguards and manages digital keys for strong authentication and provides crypto processing.
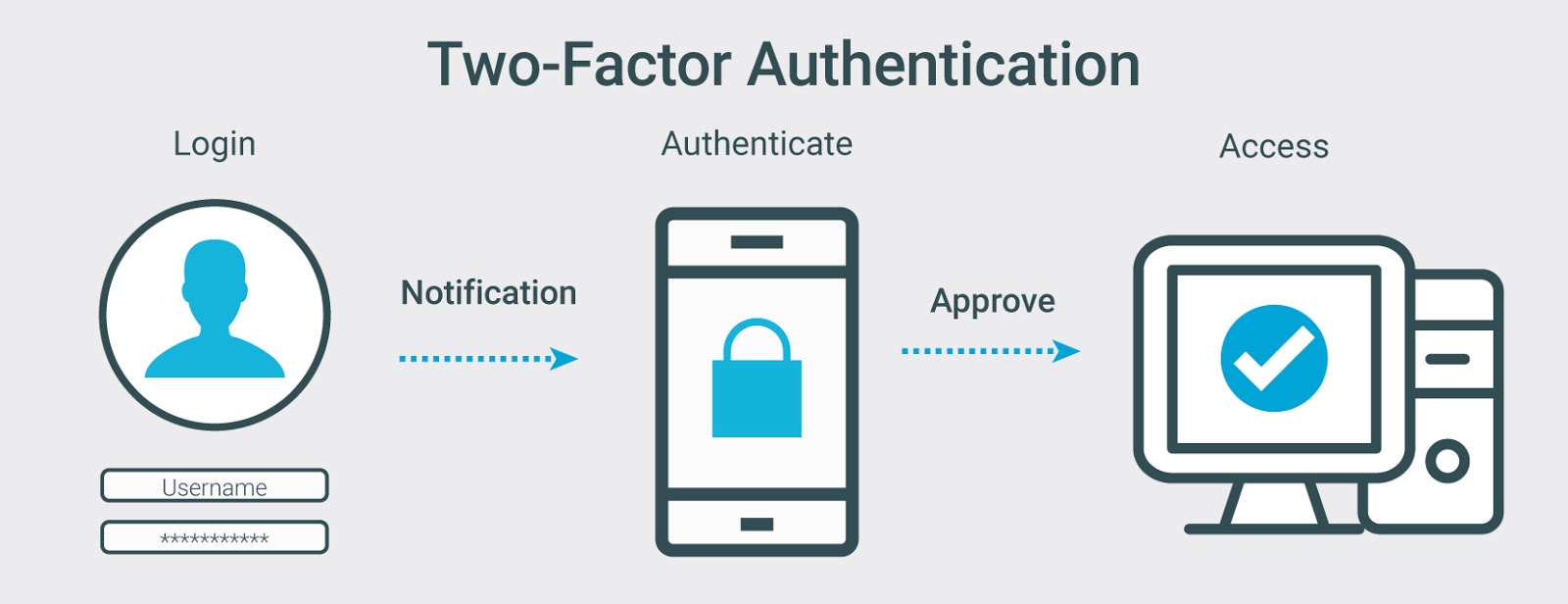
2 Factor authentication
Techium Solution provides two factor authentication mix of convenience, security, and low cost that helps companies power service activation, enable secured access to the mobile workforce, and verify financial transactions.