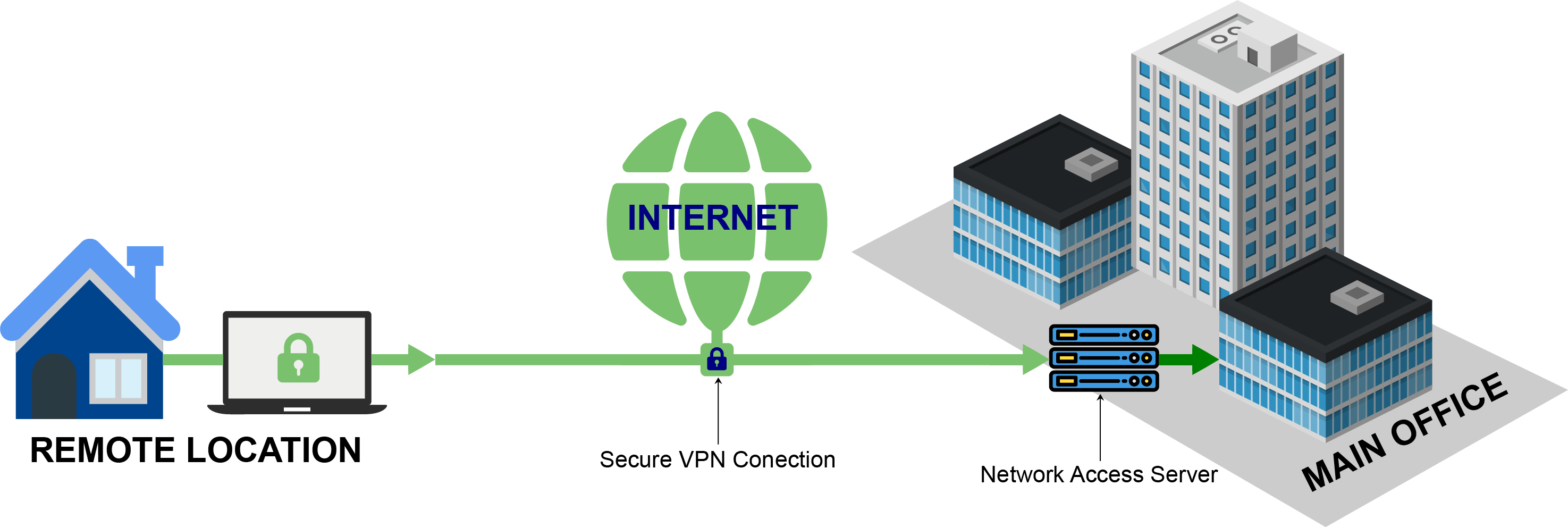
Remote Access VPN
Remote access virtual private network, or remote access VPN allows your employees to securely and privately access data on a remote network. It creates a secure virtual tunnel between an offsite employee's device and the company's network. This helps your employee connect to all your company resources without compromising data security.
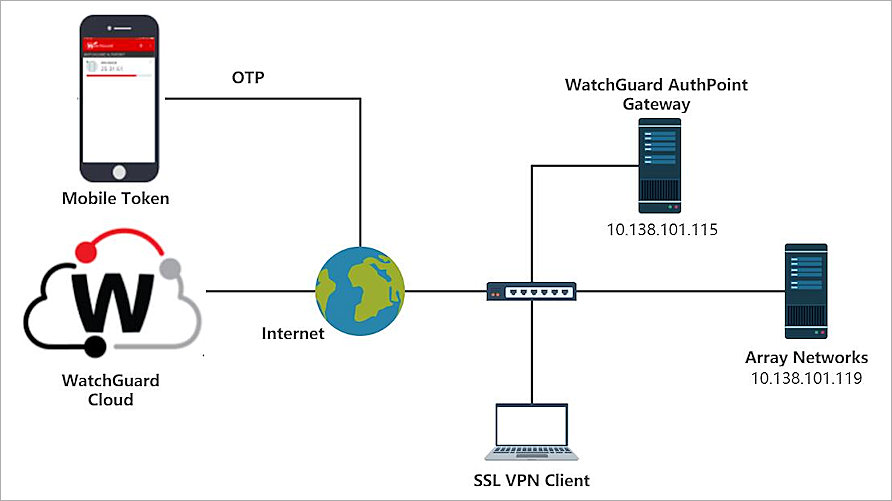
SSL / VPN
Use high class SSL VPN security with a standard Web browser. It’s used to give remote users with access to Web applications, client/server applications and internal network connections. It provides a secure communications mechanism for data and other information transmitted between two endpoints.

Mobile Security
Our mobile security solution protects your portable devices - laptops, tablets, smart watches, phones - against cyber threats. It also refers to the means by which a mobile device can authenticate users and protect or restrict access to data stored on the device. Authentication methods include passwords, personal identification numbers (PINs), and pattern screen locks. More advanced forms of authentication include fingerprint readers, eye scanners and other forms of biometric readers.
Endpoint Security
Endpoint security secures and protects endpoints, or end-user devices like desktops, laptops, and mobile devices connected to a remote network, against zero-day exploits, attacks, and inadvertent data leakage resulting from human error. It covers your entire network and protects against different types of security attacks, while antivirus software covers a single endpoint and only detects and blocks malicious files

Cloud-based Communication
Cloud-based communication models run network and applications from the cloud, thus guaranteeing better user experience for your employees. It offers faster deployment and quicker adoption. With such models, you have access to the latest software and releases, with more control on security and user management.

Virtual Secure Access Gateway
Virtual secure access gateways enable secure access to applications, desktops, files, networks and websites for your work from home employees. This provides secure connectivity, end-point and server-side security and application-level AAA policies on a per-user basis.